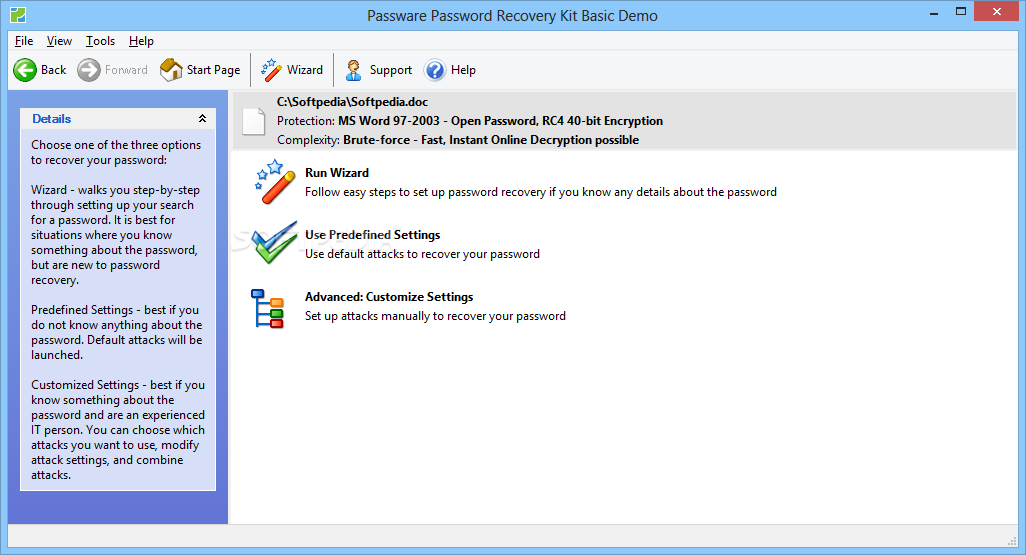
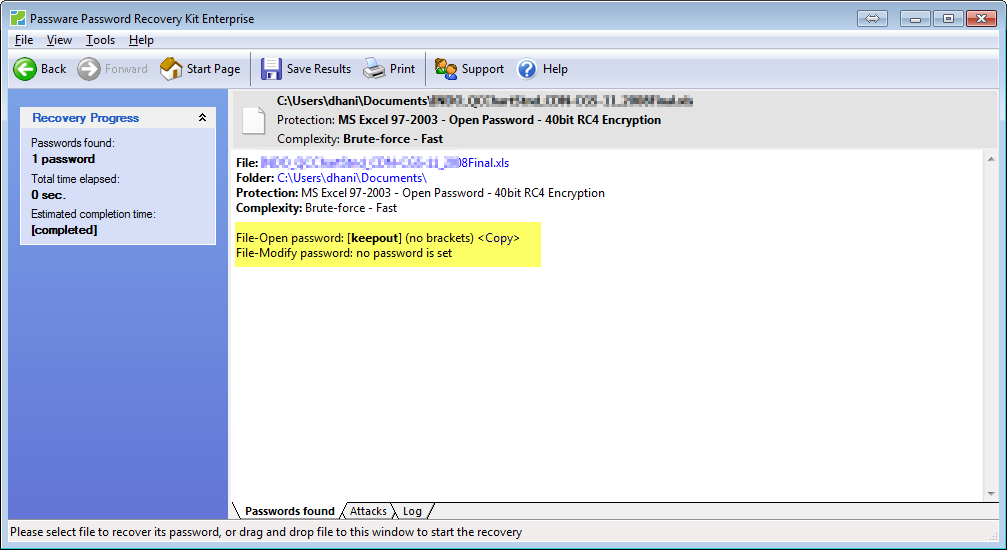
Passware Kit Enterprise Edition 8.1 Full
This complete electronic evidence discovery solution reports all password-protected items on a computer and gains access to these items using the fastest decryption and password recovery algorithms. Many types of passwords are recovered or reset instantly, and advanced acceleration methods are used to recover difficult passwords. Passware Kit Forensic introduces batch file processing and a new attacks editor, which sets up the password recovery process in the most precise way to provide the quickest decryption solution possible. The highest performance is achieved with Distributed Password Recovery, using the computing power of multiple computers, both Windows and Linux platforms.
Passware Kit Business allows system administrators, IT professionals and help desk personnel to get access to any file or server whenever required. 8: 1 year: 25: 2: 23. Passware kit enterprise 9 0 Full incl serial. Passware Kit Enterprise Edition 8.0.2514 [TNTVillage.scambioetic in Applications.
And decrypt hard disks encrypted with BitLocker, TrueCrypt, VeraCrypt, LUKS, FileVault2 and PGP. Passware Kit scans the physical memory image file (acquired while the encrypted disk was mounted, even if the target computer was locked), extracts all the encryption keys, and decrypts the given volume. Such memory images can be acquired using Passware FireWire Memory Imager (included in Passware Kit Forensic, has limitations), or third-party tools, such as, or win32dd. If the target computer with the encrypted volume is powered off, encryption keys are not stored in its memory, but they could be possibly recovered from the hiberfil.sys file, which is automatically created when a system hibernates. NOTE: If the target computer is turned off and the encrypted volume was dismounted during the last hibernation, neither the memory image nor the hiberfil.sys file will contain the encryption keys.
Therefore, instant decryption of the volume is impossible. In this case, Passware Kit assigns brute-force attacks to recover the original password for the volume. Overall Disk Decryption Steps. Acquire a memory image of or take the hiberfil.sys file from the target computer. Create an encrypted disk image (not required for TrueCrypt). Run Passware Kit to recover the encryption keys and decrypt the hard disk.
Below are the steps to decrypt a hard disk image. Please, refer to Passware Kit Help for the detailed instructions. Acquiring Memory Image Using Passware FireWire Memory Imager If the target computer is turned off, but the encrypted volume was mounted during the last hibernation, skip this step. Take the hibefil.sys file from the target computer or its hard drive image and use this file as a memory image for decryption.
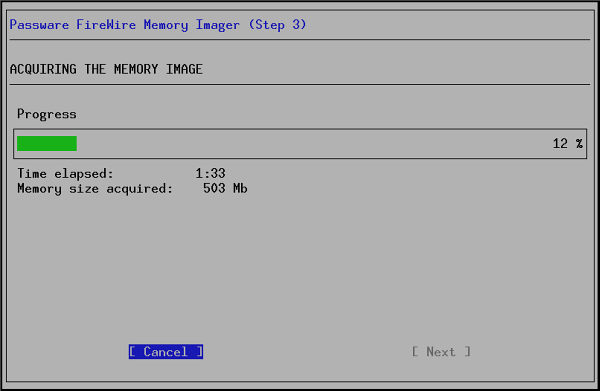
NB: Passware FireWire Memory Imager does not capture memory of more than 4GB and does not work with MacOS higher than El Capitan. Requirements for Memory Acquisition:. The target computer is turned on and the encrypted volume is mounted.
Both the target computer and the computer used for acquisition have FireWire (IEEE 1394) ports. A FireWire cable or a Thunderbolt cable. On the Passware Kit Start Page click Memory Analysis, and then click Passware FireWire Memory Imager: The following screen appears: Insert a blank USB flash drive and click Next.
Harvard trauma questionnaire. Passware Kit copies the necessary files on the USB flash drive. The Passware FireWire Memory Imager USB drive is ready: 3.
Restart your computer. Passware FireWire Memory Imager starts: 5.
Quickbooks Enterprise Edition
Connect the target computer with a FireWire cable. The memory imaging process starts: 7.
Office Enterprise Edition
Unplug the FireWire cable, remove the USB flash drive, and press Reboot to restart your PC. The memory image of the target computer (a memory.bin file) is created on the USB flash drive. Decrypting the Hard Disk Passware Kit can work with either a TrueCrypt volume file (.TC, encrypted file container), or with its image. For BitLocker/FileVault2/PGP decryption, Passware Kit works with image files of encrypted disks. Disk volume images can be created using third-party tools, such as,. Click Full Disk Encryption on the Passware Kit Start Page. This displays the screen shown below: 2.
Click on the corresponding encryption type, e.g. This displays the screen shown below: 3.
Schoollink Enterprise Edition Namibia
Click Browse and locate the encrypted volume file or its image file. Click Browse and locate the physical memory image (memory.bin) or the hiberfil.sys file from the computer to which your encrypted volume was mounted. NOTE: If the target computer is turned off and the encrypted volume was dismounted during the last hibernation, neither the memory image nor the hiberfil.sys file will contain the encryption keys. Therefore, instant decryption of the volume is impossible. In this case, switch to “The volume is dismounted” option, and Passware Kit will assign brute-force attacks to recover the password for the volume. For TrueCrypt, FileVault2 and PGP decryption, click Browse and select the location and name of the destination file (the image of the decrypted volume). This procedure initiates the decryption process.
The decryption might take several minutes depending on the size of the memory image file. The figure below shows a sample result.
Now you can open your hard disk using the encryption key recovered, or extract an image of the decrypted disk.